Last Thursday, August 8, 2024, I attended the JC Cybersecurity Training Program led by Sean Hana of Nemstar. Sean is one of Europe’s leading information security and cyber trainers, with extensive global industry experience. Nemstar specializes in information security and cyber training, boasting over 25 years in the field.
Understanding Cybersecurity and Its Importance
The program covered cybersecurity awareness, including topics such as hacking, how computers, phones, and devices can be compromised, and the potential damage and impact. We learned about system compromises and ways to protect ourselves, not only for John Clements but also for our families and friends.
Sean compared cybersecurity to government safety laws, such as seatbelt regulations. Just as governments follow up with information and advertisements to ensure compliance, cybersecurity awareness requires ongoing education. Understanding the problem reduces the likelihood of becoming a victim. Sean emphasized the importance of personal responsibility in protecting oneself, their loved ones, and their organization.
Rising Cybersecurity Threats
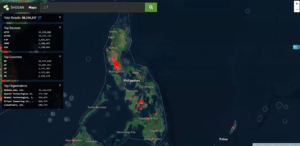
He shared that cyberattacks in the Philippines tripled in 2023, affecting various sectors, including manufacturing, hospitals, retail, healthcare, and telecommunications. These attacks often involve ransomware.

Understanding Ransomware Attacks
A ransomware attack is a type of cyberattack where malicious software encrypts a victim’s data or locks them out of their device. The attacker then demands a ransom payment to restore access. Today, it is easier to evade detection due to the use of Bitcoin and other cryptocurrencies, which are difficult to trace.
Sean recommended using websites that track global cyberattacks, such as MAP | Kaspersky Cyberthreat Real-Time Map and Live Cyber Threat Map | Check Point.

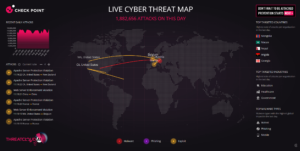
In 2024, statistics show a significant spike in malicious activity in the Philippines, primarily attributed to Chinese state actors, with incidents quadrupling in the first quarter.
Sean emphasized, “The more you understand about hackers, the less likely you are to become a victim.”

The Hack Chain: Steps in Cyberattacks
Then he started discussing hacks, stating, “What exactly is a HACK?” Hacking, or computer hacking, refers to gaining unauthorized access to data in a system, computer, or any digital device. Hacking is divided into steps or processes known as the hack chain. It consists of reconnaissance, vulnerability analysis, weaponization/exploitation, and payload delivery. These are the modus operandi of a hacker.
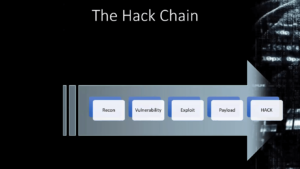
Reconnaissance: The First Stage of a Hack
The first stage of any compromise is reconnaissance or recon. In recon, the hacker’s job is to discover the target. It’s all about research—to find out everything about the target, for example, John Clements. The hacker will need to learn about its management team, customers, business, suppliers, the technology it uses, and its employees. They will research social media platforms such as Facebook, WeChat, X, LinkedIn, Google, and the dark web. They will gather information about employees, their families, hobbies, and social media posts. Alternatively, they might go to the dark web to buy information about the target. The more the hacker knows about you, the easier it is for them to trick you.
The Deep, Dark Web
There are two versions of the internet: the clean, safe version that we use every day through Google or Bing, and the deep, dark web, a hidden part of the internet that is not visible through normal searches. The dark web is not safe, secure, or controlled. It is designed for criminal activities, to conceal criminals, and is hard to navigate.
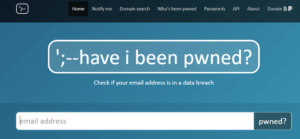
Safe reconnaissance websites include “Have I Been Pwned,” which checks if your email has been compromised in a data breach. This site will tell you if your email address has been involved in any breaches and if your information has been stolen and sold on the dark web. Tip: Do not use the same password for every account or site.

For devices, Shodan Search Engine can be used to search for unsecured internet systems and devices.
Vulnerability Assessment and Weaponization
The second step is vulnerability assessment. With all the information gathered, the hacker can find weaknesses in the target, such as weak passwords used across multiple systems or sites, weak processes, outdated software, or unencrypted data. Vulnerabilities are not just in computer systems; they exist in processes, software, and daily activities. One significant vulnerability is that nice people, such as many Filipinos, can be easily manipulated or tricked. Social engineering is a cyberattack that relies on manipulating human behavior to gain access to sensitive information or systems.

If the hacker finds a vulnerability, they will not fix it; instead, they will weaponize it, turning the weakness into a weapon like a virus. Sean referred to this as a Zero Day attack. One example Sean gave is COVID-19, which caused millions of deaths because our bodies did not have protection or an antivirus. No matter how good the IT team, system protection, firewall, or antivirus is, nothing is 100% effective.

Zero Day Vulnerabilities
Zero Day vulnerabilities are bought and sold and can be worth millions in the online marketplace. In ethical cases, Microsoft’s Bounty Programs (MSRC) buy and patch these vulnerabilities before hackers exploit them.

However, in unethical cases, hackers can buy and weaponize these vulnerabilities to use them in crimeware. Crimeware is professional hacking software bought by hackers and governments, who use it to spy on other governments or their citizens.


Targeting and Exploiting IoT and National Infrastructure
The third step is weaponizing vulnerabilities into exploits. Social engineering attacks trick people into doing things they shouldn’t. Hackers can target clients and servers, web, cloud, mobile devices, and IoT (Internet of Things) systems. Anything connected to the internet is a potential target. If it is connected to the internet, it could be hacked.

It’s not just IoT; critical national infrastructure can also be targeted, leading to disasters. For example, the US Colonial Pipeline attack in 2021 used ransomware to shut down fuel delivery, causing widespread shortages and panic. The ransom paid was 75 bitcoins (approximately $4.4 million).

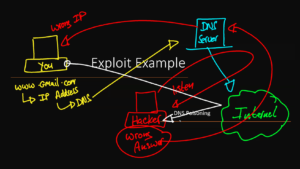
DNS Poisoning: A Common Exploit
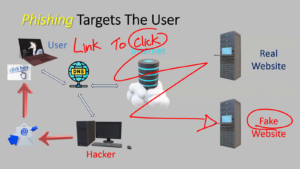
DNS poisoning is another type of vulnerability that can lead to exploits, such as redirecting users to malicious websites instead of their intended destinations. This can result in data theft, malware infections, or service disruptions. DNS poisoning is similar to phishing or spoofing, where users are tricked into clicking links leading to fake websites via phishing emails.
Delivering the Payload and Protecting Against Cyberattacks
The fourth step is the payload. Hackers need a vulnerability to exploit, and exploits are used to deliver the payload. This step is the actual danger of the cyberattack.
Hackers use codes to run on our systems and deliver payloads such as spyware to monitor activities, ransomware to encrypt data and demand ransom, and backdoors or botnets to gain remote access to systems, devices, and networks.
The Solution: Protecting Against Cyber Threats
To protect a business, such as John Clements, and to safeguard personal information, several steps can be taken. At John Clements, we use firewalls and endpoint protection on every device, ensuring they are updated regularly. Updates and patching are scheduled and monitored. We also use corporate Microsoft 365 for email encryption and data protection, which includes multi-factor authentication (MFA).
Embedding Cybersecurity into Organizational Culture
It is crucial to ensure that all John Clements employees are aware of cybersecurity practices to help protect the business. Embedding cybersecurity into our organization and developing a positive cybersecurity culture is essential. This involves educating employees through training programs and growing the IT team’s cybersecurity expertise. Identifying and securing critical assets, understanding cybersecurity threats, and managing risks by implementing effective cybersecurity measures are vital. John Clements should also collaborate with partners and plan responses to cyber incidents.
Sharing Cybersecurity Knowledge Personally
On a personal level, sharing knowledge about cyberattacks with family and friends is important. Advise them not to connect to free public Wi-Fi, as nothing is truly free. Teach them to use strong and unique passwords and enable multi-factor authentication for added security.
John Clements Consultants aims to share insights and tips on how to protect organizations against cybersecurity threats. Visit our website for upcoming events and training programs.



